No Keys Required.
Unlock the possibilities of keyless entry. Smart Locks seamlessly integrate with our smart home security system giving you control from anywhere. No need to give house keys to service providers, neighbors, or even your teenage children. Available with our smart home packages.
LEARN MORE
One App Does It All.
Control all your security and smart home devices from one mobile app. Set specific scenes and schedules for your security system, smart lighting, thermostat, smart locks, and more utilizing Z-Wave technology.
LEARN MORE
Keep an Eye on Things.
Use our high-definition cameras to keep an eye on things from wherever you are. Instantly connect to your wireless home camera system to capture live video and access recorded video. Available with our premium package.
LEARN MORE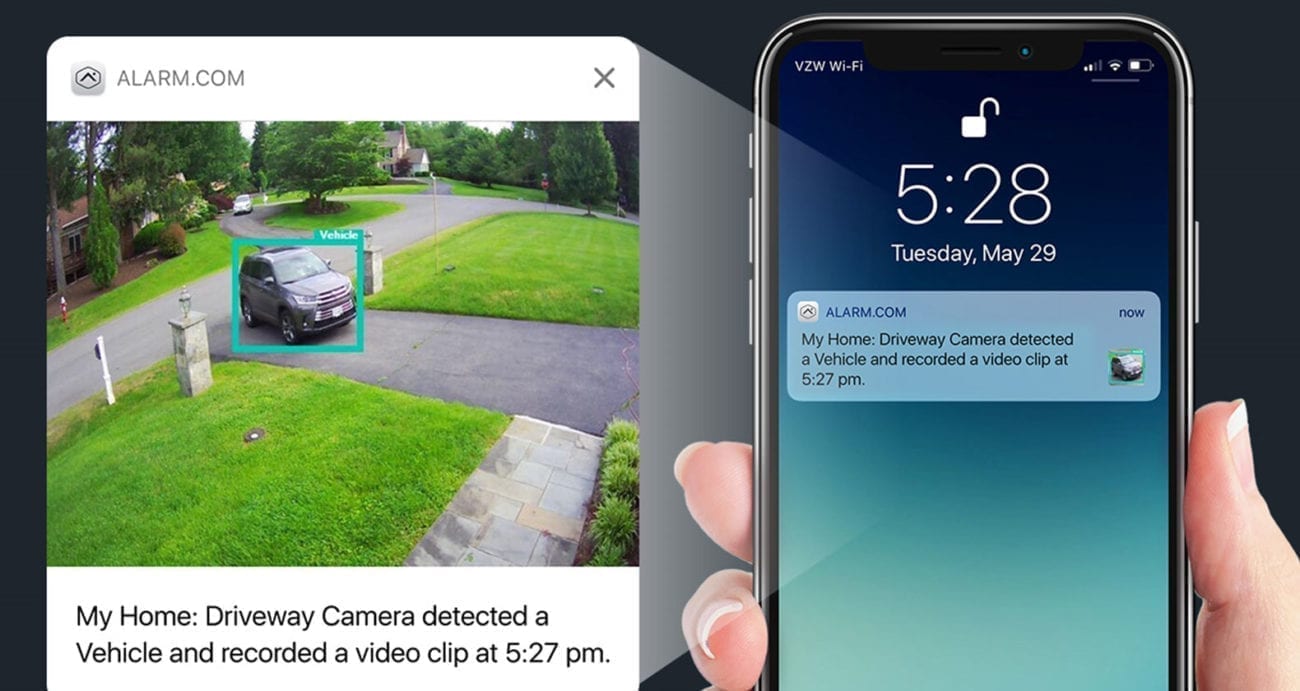
Get Smarter Video With Video Analytics.
Motion-sensing outdoor cameras will notify you if a person, car, animal, or unidentifiable object crosses your camera’s path. Available as an add-on to any of our packages.
LEARN MORE
Alexa, Dim The Lights.
Experience the ultimate in-home connectivity and convenience. Our smart systems can integrate directly with Amazon Alexa and Google Home helping to remotely control your home security system, thermostat, lights, door locks, and more from a simple voice command.
LEARN MOREExperience The Johns Brothers Difference
“We believe everyone has the right to protect their homes and families at a fair price without having to settle for substandard customer service.”
- 24/7/365 UL-Monitoring Center Services
- Delivering security and quality customer service for over 40 years
- We treat our customers like people, not account numbers

PREMIUM PACKAGE
Our most complete package featuring protection, automation, and video delivered straight to your smartphone.
LEARN MORE
SMART PACKAGE
Our most popular package offering more than protection. It’s your pathway to home automation.
LEARN MORE
INTERACTIVE PACKAGE
The essential security package featuring affordable protection with a wireless connection.
LEARN MORE